The Basic Principles Of Sharepoint Data Migration
This will help you establish cutover days for all web content as well as customers and deal with any kind of dangers you have actually identified, such as websites or data shares that need to be rubbed, legal hold or e, Exploration problems, and even holidays or other vital company days or occasions that you need to think about.
Your organization may choose to have customers in some organization units manually move their material to One, Drive or Share, Aim from share network files or other sharing apps, while other service systems with lots of TBs of consumer web content or sensitive IP may like that IT and also security teams function with each other to relocate material to its brand-new location.
You can ask individuals to by hand upload their data to Share, Factor or One, Drive. This functions finest for smaller sized documents like basic Word files, Excel spread sheets, and also Power, Factor discussions. Relocating tiny specific files For private users who have a whole lot of web content to relocate, they can set up the One, Drive Sync App for Windows or Mac to drag and drop documents from documents shares or their computer system's Data Explorer to One, Drive.
The Buzz on Sharepoint Data Migration
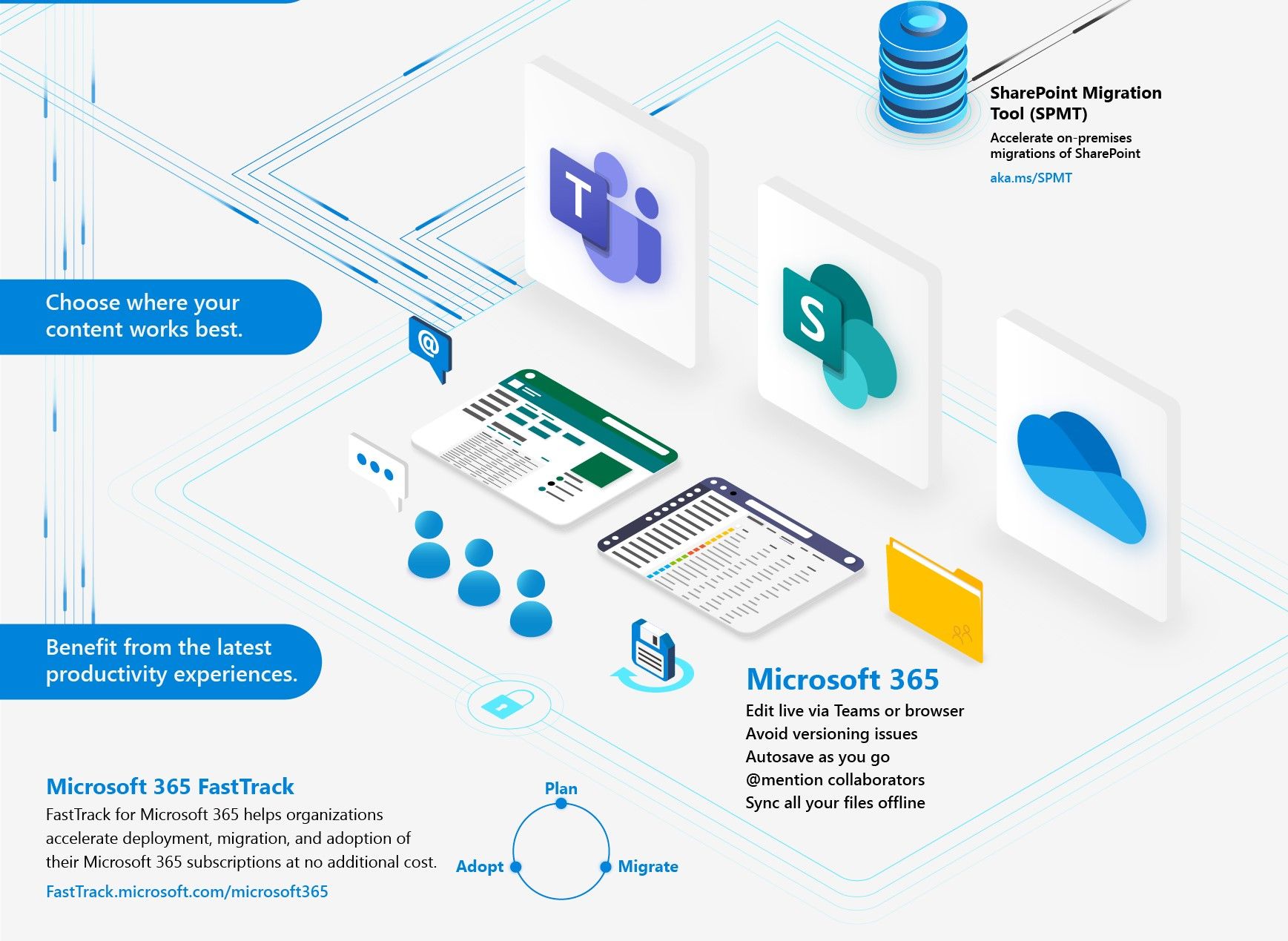
Moving an individual data library to the cloud You can use the Share, Factor Migration Tool (SPMT) to move your data from Share, Factor on-premises record libraries, lists, or normal files shares. You can additionally make use of the new Power, Covering cmdlets based on the Share, Factor Movement Tool (SPMT) movement engine to move documents from Share, Point 2010 and also Share, Point 2013 on-premises document collections and checklist products, and data shares to Microsoft 365.
It also consists of the Share, Point Movement Identity Administration Tool, that executes identification mapping by scanning Share, Point, Energetic Directory Site, as well as Azure Active Directory Site. Evaluating Share, Factor Server 2010 and 2013 web content prior to movement Available in the Share, Point Admin center, Movement Supervisor gives a central means of linking servers, developing jobs, as well as instantly distributing your movement tasks.
Moving information from other cloud solution companies The Microsoft Azure Information Box is a service that lets you order a gadget from the Microsoft Azure site (sharepoint data migration). You can then duplicate TBs more tips here of information from your servers to the gadget, ship it back to Microsoft, and also your data is replicated into Azure.
Eliminating the dependence on your WAN link to transfer information when moving files Relying on the device you choose to make use of for your migration and your company's business needs, you may wish to intend your migration during off-work hours or on weekends, ideally, simply to stay clear of disrupting daily service. sharepoint data migration.
Little Known Facts About Sharepoint Data Migration.
Whenever and also nonetheless you determine to relocate web content, you must likewise produce a communications plan, offering individuals plenty of innovative notification as well as explaining what they should anticipate as well as when. If you have a modification management team, you can likewise collaborate with them on guaranteeing that paperwork and training products are readily offered when the movement begins (sharepoint data migration).
An effective pilot can assist develop confidence, specifically with leadership and various other essential stakeholders, and also can assist you reduce threats. Select individuals from across the company who possess information that they are sharing with each various other and/or with outside parties so you can examine exactly how authorizations transfer. You can keep your pilot running also throughout the actual migration simply to help decrease surprises.
The Facts About Sharepoint Data Migration Uncovered
Migrating to Share, Factor Online from on-premises or other systems can be a complex and tough process, however it can also bring several benefits such as increased adaptability, scalability, as well as safety. As a method supervisor, IT Director or CIO, blog you are in charge of ensuring that the movement achieves success, smooth, and also lined up with the company's goals and also useful reference requirements.
Plan the movement method: Pick the best movement approach based upon the scope, goals, as well as analysis results, taking into account aspects such as data dimension, complexity, as well as urgency. Prepare the target atmosphere: Ensure that the Share, Factor Online setting is effectively set up, enhanced, and also all set to obtain the moved information and also content.
Map the data and also material: Create a thorough map of the information and also content that you desire to relocate, consisting of the area, framework, partnerships, as well as metadata. Choose the right devices: Select the proper tools for the migration, such as Microsoft's Share, Factor Movement Device, Share, Entrance or Ave, Factor, relying on your certain demands and also demands.